

Citrix Policies are not the coolest thing to mess with but they are very important and are very often overlooked from a security perspective. I hope this quick blog will help you look at your policies differently and help you secure your deployment. When I’m doing Citrix Security Assessments the weak policies are usually the second biggest finding (After Patching) because they usually are just defaults and or the filters and or their order make them weaker than most clients expect them to be with some of those factors.
In this article, I will go over the basics of the Citrix security policies, the scary ones you should worry about, how to check if you’re at risk and how to fix them up. Many of these settings are enabled by default because most customers need these settings but if you look at them just one more time in most cases you should be able disable many of them.
Citrix Policy Big 4
- Copy\Paste
- Bi-directional
- Copy\Paste Write Allowed Formats – All
- Drive Mappings
- On by Default
- Major
- Client Fixed Drives
- Client Network Drives
- Client Removable Drives
- Minor
- Client Floppy Drives
- Client Optical Drives
- USB Mounts
- Disabled by Default
- Restrict the Devices
- Others
- Printer Mapping
- LPT Mapping
- COM Mapping
- Microphone Mapping
- Audio Mapping
- Major
- On by Default
Citrix Policy Security Severity Chart
| Risk | Setting | Default Setting |
| High | Copy\Paste | Allowed |
| High | Copy\Paste Write Allowed Formats | Blank |
| High | Client Fixed Drives | Allowed |
| High | Client Network Drives | Allowed |
| High | Client Removable Drives | Allowed |
| High\Medium | Client USB Mapping | Prohibited |
| High\Medium | Printer Mapping | Allowed |
| Medium\Low | Client Floppy Drives | Allowed |
| Medium\Low | Client Optical Drives | Allowed |
| Medium\Low | LPT Mapping | Prohibited |
| Medium\Low | COM Mapping | Prohibited |
| Medium\Low | Microphone Mapping | Allowed |
| Low | Audio Redirection | Allowed |
The severity of some of these items will vary based on the setting and if these items are in use or if they could be used in a way to harm your company.
Depending on if you used a template from Citrix for user experience you just have an environment that has been migrated\upgraded over and over you most likely could have a problem and not even know it. From what I have seen at hundreds of deployments is that the Citrix deployment hosts the most critical items within most businesses internally and or externally.
We will dive into each of these briefly and then go into the extreme detail later which will be in the Citrix Hardening guide.
- Copy\Paste
- In some cases, it is actually needed but in most it can be disabled or tuned for directionality along with restricting different paste formats beyond just text.
- Client clipboard write allowed formats
- Blank by default which means screenshots can be easily exfiltrated out if your giving someone a desktop session or access to an application without execution being prevented from many windows subsystems that can take advantage of this.
- It is highly recommended to only allow CF_Text. If the Microsoft Suite must be used beyond just text then add CFX_OfficeDrawingShape as the other format.
- Many of these other methods are ways that payloads can be sent to the server\desktop or data can be sent out beyond just text. Who would have guessed there were 23 things to Copy\Paste?
- CF_TEXT
- CF_BITMAP
- CF_METAFILEPICT
- CF_SYLK
- CF_DIF
- CF_TIFF
- CF_OEMTEXT
- CF_DIB
- CF_PALETTE
- CF_PENDATA
- CF_RIFF
- CF_WAVE
- CF_UNICODETEXT
- CF_ENHMETAFILE
- CF_HDROP
- CF_LOCALE
- CF_DIBV5
- CF_OWNERDISPLAY
- CF_DSPTEXT
- CF_DSPBITMAP
- CF_DSPMETAFILEPICT
- CF_DSPENHMETAFILE
- CF_HTML
- CFX_RICHTEXT
- CFX_OfficeDrawingShape
- CFX_BIFF8
- Drive Mappings
- This is the absolute best way for employees and or attackers to get things in and out of your environment. In most cases it isn’t needed but is never disabled. I have seen clients where they actually need it to just map their Local Drive only and all the other mappings could be disabled. Who has a floppy or optical drive anymore, can we at least turn those two off?
- Think about what data the user has access to on their local computers, in many cases you may or may not be able to control those endpoints in many service provider models to third party entities.
- Most users will have some mapped drives on the local computer that will be mapped by default and who knows if your security team wanted a Citrix session to bridge that gap from a network share to their endpoint.
- How many SMB shares have Everyone for Share permissions along with the actual File Permissions?
- You could use https://www.mcafee.com/us/downloads/free-tools/sharescan.aspx to help find them on your network, there are also more advanced ways but this is one of the easier tools to run. Make sure you let your security team know before you start blasting scans off so you don’t have to update your resume depending on your INFOSEC policies.
- What kind of data do you have, and what compliance body does it fall under? (HIPAA, PCI and many others)
- This can make drive mappings being enabled much more severe.
- USB Mounts
- The good thing is that by default this setting it to Prohibit these mappings.
- Most organizations have DLP (Data Loss Prevention\Protection) policies and a USB drive is in most cases prime candidate number 2 after email for data exfiltration.
- There are many ways that mapping USB devices can also introduce instability along with other possible attacks, so filtering devices if they must be enabled is your safest bet.
- If you are just doing voice Dictation with a Philips device, bar code scanners, credit card readers and many other must use cases you should just allow that specific device only.
- Other Items
- Printer Mapping
- This is enabled by default and in many cases, this is needed for Application X to work and for the user to do their job. If you have an application that doesn’t need to print then disable it or at least just limit it to just the applications that need it and exclude if from everything else.
- LPT Mapping
- Mapping these old school physical printer ports are enabled by default but I haven’t seen them actually used in a couple hundred deployments since most printers now are Network or USB only now. I have had great success disabling this in a lot of deployments and like always if you don’t need it disable it.
- COM Mapping
- This is disabled by default so usually I don’t find it enabled but I do see it every now and then for some medical devices and in manufacturing. If it needs to be enabled just filter it to the servers\desktops that need it.
- Microphone Mapping
- This is great for Video Conferencing along with Dictation but in many cases, it may not be needed and should be disabled. This may not seem very security related being able to record your voice in applications but it is a way that data can come in. I have been working on some testing and will have more information later in the VDI Lockdown guides.
- Audio Mapping
- This also may not seem like it is very security related item too, but in many industries an audio stream can be very sensitive data. I have seen the medical, legal, banking and science\research industries use dictation, but they have some serious Patient and Intellectual Property information in them. If someone can listen to the audio and or if you have mapped drives enabled they can pull the data out. This is a stretch in many cases but we don’t like loose ends.
- If you don’t need sound I would recommend turning it off but if you’re doing a desktop experience it will be needed but I would just recommend thinking about what audio you may have that is confidential that you don’t want to get out.
- Printer Mapping
- Sometimes audio has to be mapped to hear error messages for basic application functionality.
What to do?
Secure it by Default!
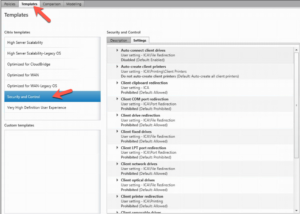
In many cases when I’m doing security assessments I don’t just enable the “Security and Control” Policy Template and call it done\more better, because it could cause mayhem if people do have legitimate uses for some of these security controls. Depending on your setup and how far along your deployment is, you may be able to apply this use this template as a baseline to help secure things when you start off. Starting off your Citrix deployment off with this policy if you can and open it up per Application\User Group to open things up as needed.
Next Blog
I’m working on a couple other things that I will publish on my blog VDISecurity.org and within CUGC too.
- Citrix Policy Lockdown Examples and Guide
- Citrix Patching
- Citrix WEM and AppLocker Lockdown
- Citrix Antivirus
- VDI Lockdown Guide (Everything rolled into an updatable one stop shop)
Appendix
Thanks for all the work that Carl Webster does on keeping up with his documentation scripts and policy lists and much more.
Policy Listings
http://carlwebster.com/downloads/download-info/citrix-default-user-policy-settings/
http://carlwebster.com/downloads/download-info/citrix-default-computer-policy-settings/
http://carlwebster.com/downloads/download-info/citrix-policy-settings/
Documentation Scripts
http://carlwebster.com/downloads/download-info/xenappxendesktop-7-8/
Always a great overall with some good Policy information in it.