Citrix Released Insight Services for HDX (Citrix) and Web Traffic a couple years ago and it was and is a great solution but I think they have finally doubled down. They were able to see the value of the data they had from the NetScaler AppFlow streams. This is a great step for them in the security realm, pricing and packaging will determine how many of their existing deployments they can get this deployed in and how many new customers are drawn. When I compare Citrix and VMware right now, VMware has NSX which is an advantage in how they package it but you can run it with Citrix too but at a higher cost because of the packaging. This more adaptive security model is very appealing and if you have NSX and this you are doing what you can for sure but it doesn’t mean you are unhackable either. I believe this is one of the best bolt on things they have ever added and if the pricing and packaging is right it will be a hit.
Here are some of the slides from Citrix Synergy 2017 as we go into this.
https://www.citrix.com/products/citrix-workspace/form/citrix-analytics/
Going over the same scenario we will below from the Stage at Synergy.
https://www.youtube.com/watch?v=wTMo6JVIs_Q
This first console looks great, we can see Users, Applications, Data and Networks which looks very familiar to Insight Services. This is laid out like Director which is familiar with a Sprinkle of Citrix Cloud within the header and the body of this view.
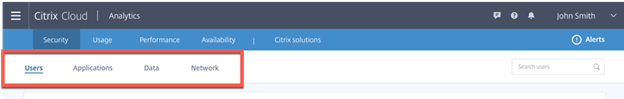
I like to see the Highest level of warning next with High Risk, Medium Risk and Low Risk with the big two in my mind at the end with Watchlist and Quarantined. I’m assuming Watchlist are users that haven’t had a high enough score to be fully Quarantined yet.
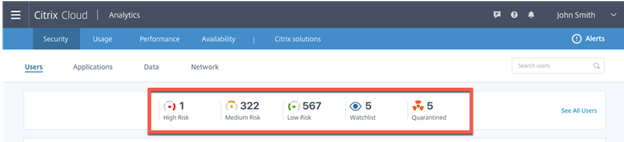
Then we have latest Alerts. This looks like some of the Alerts that were added to Director 7.9 and should be able to open cases and do things very easily with your monitoring solutions. Depending on your SIEM or Monitoring solution just triggering off of some of the keywords or the numbers within this alert should help be able to easily trigger other actions outside of the Citrix Bubble.
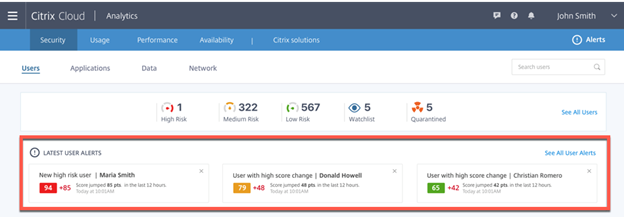
Then we have the Three Columns that are near the bottom which show our “Top High Risk Users” (Looks to be people in the 70’s and higher cumulatively and ones in the Orange Zone) , “Top Users with High Score Change” (Users that have went from Hero to Zero in not time and also show the number of qualifying events that got them there.) and “Users in Watchlist with Highest Score” (This one seems pretty simple people who have been added to the watchlist sorted by Higher scores, based on this mock up 5 users are on the watch list.)
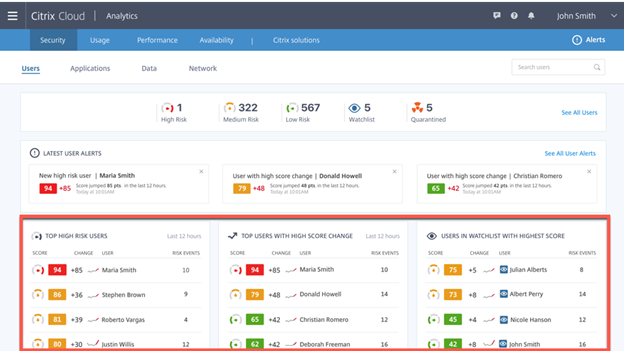
Now we start figuring out what is up with our highest scored user. She is on our Latest User Alerts with a near 100 (Worst it can be, Not an A+ but a F+) She is on 2 of the 3 user charts at the bottom also based on her high score and the amount of change. She is way beyond the watchlist because she is quarantined
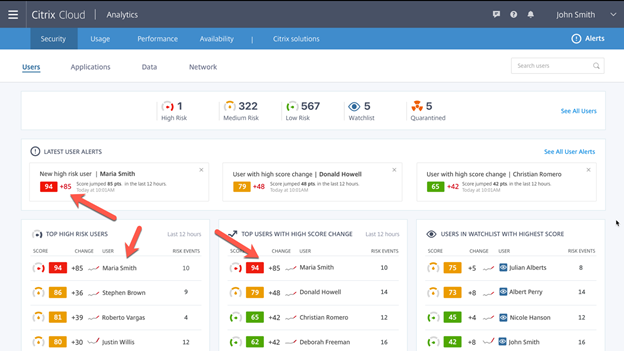
Once selected we can see a whole lot of valuable data about her. Let’s dissect this view of the management console also.
Quick ways to be able to Quarantine, Add to Watchlist, Add Tags and Add Notes about the user quickly based on the data that is displayed here. If I could change something I would add something in this middle with their current highest security status and Icon like Quarantined and WatchList and then on the right adjust those fields based on which list they are on with it already highlighted. You cannot add to the Quarantined list if they are already Quarantined.
The next section looks like it is just a legend for the icons used for each of the violation groups or whatever they will call it. Access, Applications, Data and Network.
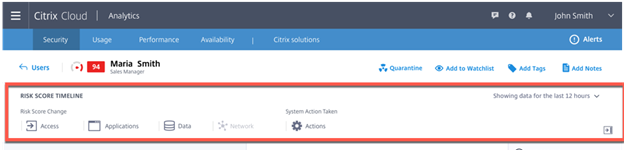
On the Right-Hand User Pane there is a ton of Data here that is very helpful.
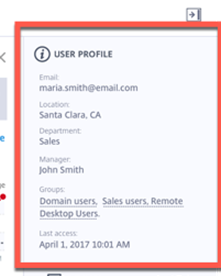
User Profile – looks to be pulling from some of the same things that Director does on the basic user information. I think they will need to change the Groups around for large companies, because users will be in hundreds of groups, I would just stick with the top 4 and or be smart and figure out which ones entitled them to the Citrix resource and just show them and or just show everything when running reports if that is possible. Great for places with 3 groups but depending on the pricing and packaging it may be some of their first set of problems. Maria – is a Remote Sales User based out of Santa Clara California and John Smith is her manage and her last access was April 1st 2017 at 10:01AM.
Devices – This is something that a lot of people will like to see and want to run reports on even on just the Citrix Nerd side and not the Security Side. I think showing the Top 4 is fine and when you get into reports could be great. I think many Healthcare clients will blow this field up with GenShares (Computers that are used by many people using Single Sign-On Solutions like Imprivata and Caradigm) some users I have seen do 15-50 Tap-n-Gos a day so they use 20-40 Machines in a shift. So I would keep going with the numbers of the top 4 and showing the 1 that is associated with the risk score. Maria – One Unknown device just used once but based on the next section it should have been 2 (India and Russia) or the travel to India was legit. Cannot tell here.
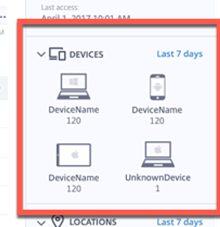
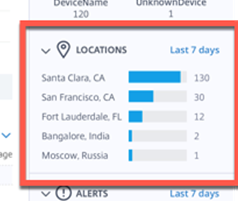
Location – This is some great data and I cannot think of problems right now with this. The thing I want to know is what GeoDatabase is it using and can we as admins add known Subnets and Office names to it to help make it more relevant in a hurry. In the world of Double-hop-DMZ’s, LANs, WANs and NATs sometimes users are all over the world but look like they are from one place. Maria – Normally works in California and sometimes in Florida but India and Russia doesn’t look normal.
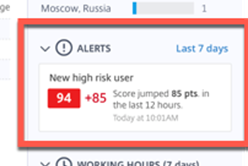
Alerts – Always and forever a good thing, I wonder what happens with more than one? I want to see how it reacts to a really bad user. This would also be my next questions into accepting someone’s bad behavior and how to bring them back from the Quarantine and make them more better. Maria – Has gained 85 Points in the past 12 hours and most likely just based on that point jump isn’t allowed to get in.
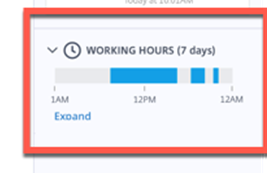
Working Hours – Very Helpful. I think this will help a lot of people and this is also another dataset that Citrix Admins would be interested in to report on for capacity planning and maintenance planning of Delivery Groups and or Published Applications. Maria – Works in the afternoon and takes a break and works later a night before midnight.
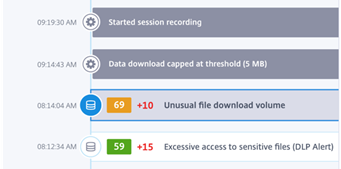
Unusual File Download Volume – I wonder if this is always static of if since this was one of the later items to increase the users score if that is why it is there. I wonder if it is a big Access Violation if it would show something cool about Access using some of the historical and real-time data like the User Details pane on the Right-Side. I need to get my hands on this to really know. Maria – Normally She doesn’t do more than 10MB and today something is going on that is the normal.
Risk Score Timeline – aka Kill Chain in the security world. I like the way it is organized and I think it does a great job of showing the data in a readable format and makes sense. I just want to see behind this PowerPoint slide curtain and see how the settings are out of the box and what is tweakable and get it in a couple deployments to see the number of false positives on Day 1 and Day 30 and beyond.
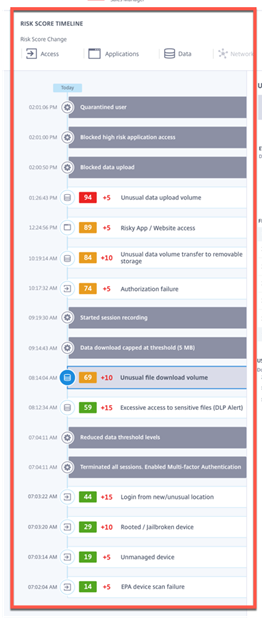
No we can dive into the Risk Score Detail Sections with Citrix Analytic Services (Citrix CAS)
703AM – The client failed the Endpoint Analysis Scan Failed, it got another Ding because it was an unmanaged Devices and that it was Rooted\JailBroken and it was from any unusual location.
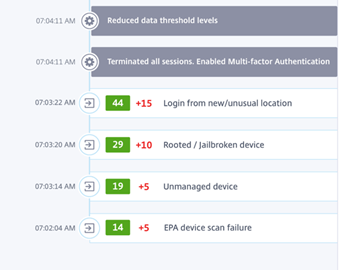
704AM – CAS killed the user session and enabled MFA (Try to see if the user is the user and if that have access to the MFA solution) and reduced the data thresholds (How much data goes through the session, to see if the user makes it through MFA and starts exfiltrating data we need to get more restrictive)
812AM – The client starts doing some unusual Data transfers and the DLP Alerts kick in so they started the session recording at 914AM.
1017AM – User had an authorization failure on top of using a USB drive to copy data too.

1224PM – User went to some shady websites and started doing some unusual upload traffic also.
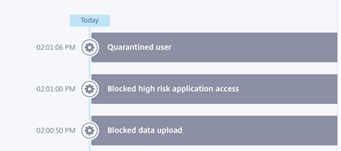
2PM – The User has been blocked from Data Uploads, High Risk Applications and the Quarantined the users.
I’m ready to see Pricing and Packaging. What we know is you have to have NetScaler and I would guess a higher edition if we looked at HDX and Web Insight services and the retention and reporting period limitations between them. I think of what could be possible with OctoBlu with this with a little work and your ticketing systems and other systems to help really do some amazing things. Hours of now human intervention spotted this deviation and blocked them which is great but just like with most things your mileage will vary and some tuning is required. I want to see the out of the box setup and the configuration process. I have signed up for the early access program and I will blog away when I get it cooking.
If someone out there in the Citrix Internets can get me on the list please give me a shot, I will not disappoint, this is my Jam!
Hopefully this helps some of you out wondering what was announced and shown at Synergy as we wait for more details I think I did a semi Ok job of deconstructing Citrix CAS with some PowerPoint images.